There are many reverse proxy products/projects available in the industry - both open source as well as commercial. In this article, we describe all the possible scenarios for reverse proxy for PicketLink IDP.
Apache HTTP Reverse Proxy Support for PicketLink IDP

If JBoss EAP or WildFly AS is used to host PicketLink IDP, you can use CLIENT_CERT authentication for the IDP. The IDP can be fronted by a reverse proxy such as Apache which can do the SSL Authentication and forward the client certificates over to the IDP. Please follow the article on SSL Mod Proxy Forwarding.
As depicted in the diagram, the reverse proxy based on apache httpd can send the client certificates via a request header called "ssl_client_cert". The IDP is configured with the SSLValve which extracts the certificates from the request header and places in the request attribute (javax.servlet.request.X509Certificate) that is expected by the SSL Authenticator.
Header Based Authentication
Sometime you want to front PicketLink EAP running on JBoss EAP or Wildfly AS with a 3rd party security system such as CA SiteMinder, RSA ClearTrust, Oblix, Oracle SSO etc which have web server plugins etc and pass authentication information via request headers. In this use case, you can use the Generic Header Authentication for PicketLink IDP.
Use Case 1: Proprietary plugins in Web Server
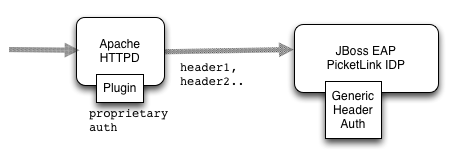
In this use case, there may be one or more proprietary plugins operating in a web server such as Apache HTTPD. The plugins perform authentication and pass information to JBoss EAP or WildFly AS via request headers. The PicketLink IDP can be configured with the GenericHeaderAuthenticator to take the authentication information from the request headers.
Use Case 2: Proprietary Security Systems
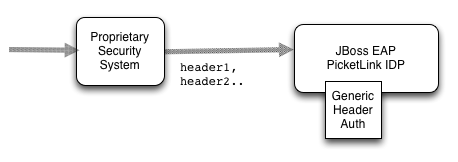
In this use case, proprietary security systems may perform authentication and then pass authentication information to the IDP via request headers.